Which of the Following Best Describes the Threat Modeling Process
Threat intelligence asset identification mitigation capabilities risk assessment and threat mapping. It takes inputs and generates outputs for each step in the process.

Threat Modeling 12 Available Methods
Repudiation Process Flow Diagrams are used by _____.
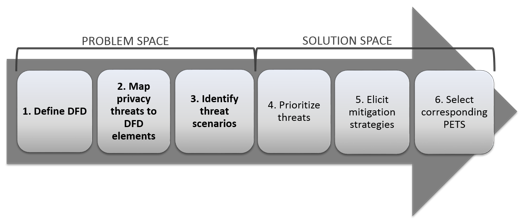
. A list of potential threats. A requirements model is the foundation of the _____ methodology. The five major threat modeling steps are shown in Figure 1.
Penetration testing falls under which all-encompassing team Heather is performing a. Performing threat modeling on cyber-physical systems with a variety of stakeholders can help catch threats across a wide spectrum of threat types. Including how severe a threat is and how much damage it could do.
Threat modeling is a procedure for optimizing application system or business process security by identifying objectives and vulnerabilities and then defining countermeasures to prevent or mitigate the effects of threats to the system. Architects can use documentation to create secure designarchitecture and mitigate architecture related security threats. The process of identifying assets and threats in an organization is known as _____.
Analysis of actions taken. 1Fixed 2Iterative 3Seldom refined 4Deterministic. Trike Which of the following are the advantages of.
Surveying or over-viewing of the application. Attack Which of the following issues can be addressed using an efficient logging system. Threat Modeling process can.
A requirements model is the foundation of the _____ methodology. A security analyst for a large financial institution is creating a threat model for a specific threat actor that is likely targeting an organizations financial assets. The 12 threat-modeling methods summarized in this post come from a variety of sources and target different parts of the process.
False A requirements model is the foundation of the _____ methodology. Start studying the Cybersecurity Chapter 2 Test flashcards containing study terms like Penetration testing is the practice of finding vulnerabilities and risks with the purpose of securing a computer or network. Which of the following security property does Spoofing violate.
_____ describes a process in which the options one faces in the current situation are limited by decisions made in the past. Which of the following security property does Spoofing violate. Path dependence According to the VRIO framework to fully exploit the competitive potential of its resources capabilities and competencies a firm must ______.
Which of the following best describes the threat modeling process. Clear objectives help you to focus the threat modeling activity and determine how much effort to spend on subsequent steps. Which of the following best describes the threat modeling process.
Create an application overview. The threat modeling process is iterative. Q1 The following is a part of a threat model except _________.
Iterative best describes the threat modeling process. The purpose is to provide a dynamic threat identification enumeration and scoring process. The iterative threat modeling process.
Identifying threats and vulnerabilities. Which of the following BEST describes the process by which code is developed tested and deployed in small batches. Analysis of actions taken.
1Process Flow Diagram 2Sequence Diagram 3Data Flow Diagram 4Entity Diagram. It is better to perform threat modeling from the early stages of the SDLC. Threat modeling is a method of optimizing network security by locating vulnerabilities identifying objectives and developing countermeasures to either prevent or mitigate the effects of cyber-attacks against the system.
The Process for Attack Simulation and Threat Analysis PASTA is a seven-step risk-centric methodology. Threat Modeling Interview Question-Answer. Correct Answer is b Iterative.
Mitigation steps for each threat. Which of the following best describes the threat modeling process. A typical threat modeling process includes five steps.
_____ generates a map that illustrates how the user moves through various features of the application. Threat modelling is an iterative process and documentation forms an important aspect of the teams responsibilities. Microsofts process of threat modeling can be utilized to do the process of threat risk modeling which performs below important tasks.
Upon completion of the threat model security subject matter experts develop a detailed analysis of the identified threats. Describes the designs object model. Application Threat Models DFDs can be used to determine the timingsequencing of the processes.
Threat modeling is a structured process through which IT pros can identify potential security threats and vulnerabilities quantify the seriousness of each and prioritize techniques to mitigate. Memorize flashcards and build a practice test to quiz yourself before your exam. Identifying the security objectives.
Answered Mar 17 2021 by sharadyadav1986. AIdentify threats b Provide countermeasures c Stop threats from happening Real Time d Help in flawless coding asked Mar 17 2021 in Threat Modeling by sharadyadav1986. Logical View Create a logical map of the Target of Evaluation.
Each of these provides different insights and visibility into your security posture. _____ generates a map that illustrates how the user moves through various features of the application. Identify the Use Case Assets to Protect and External Entities.
Here is a step-by-step process that will help you understand how you can perform a Threat Modeling and Security Analysis to determine your security requirements. The first step to perform threat modeling is to identify a use case which is the system or device that is the subject of your security. The following subsections show the details about 41 approach and how this could help in the threat modeling process.
It outlines the possible attacks that could be made on your applicationsystem. Threat modeling helps to identify the security requirements of a system or process -- anything that is mission-critical processing sensitive or.
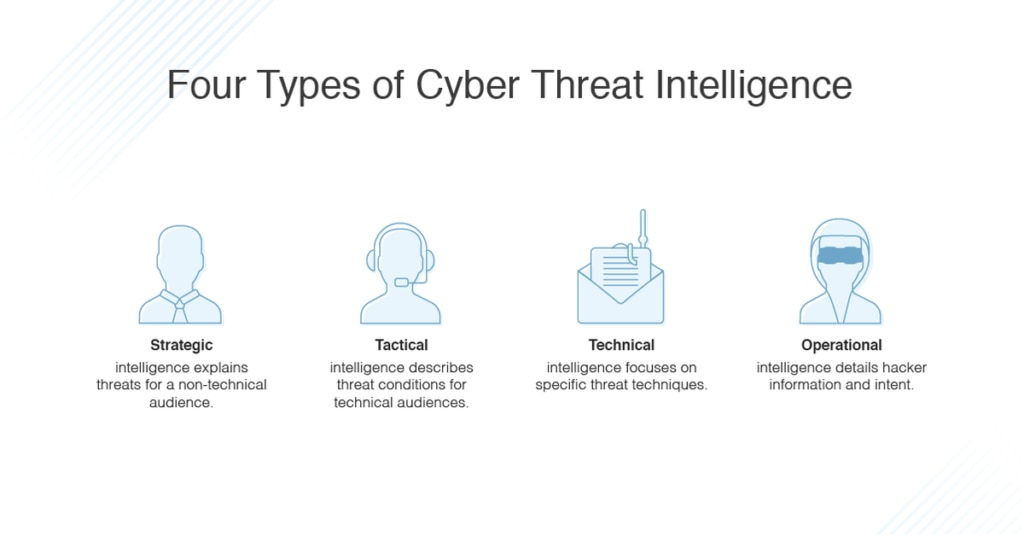
What Is Threat Intelligence Definition And Types Dnsstuff

No comments for "Which of the Following Best Describes the Threat Modeling Process"
Post a Comment